2 minutes
Unauthorised creation of courses in Sage DPW - CVE-2024-56883
Affected Product: Sage DPW
Affected Versions: < 2024_12_001
Fixed Version: 2024_12_001
CVE-Number: CVE-2024-56883
Severity: 4.3 (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:N)
Discovered by Regina Kohl, BSc and Maximilian Zingerle, BSc
During a penetration test for a customer, the audit team discovered an incorrect access control vulnerability in Sage DPW that allows unauthorized modification of course assignments between users.
Proof of Concept
It is possible for a user with the MA role to create a course for another user who also has the MA role, even though the latter does not have the option to do so in the user interface.
To do this, a valid request to create a course simply needs to be intercepted with an HTTP proxy and the user’s own ID must be exchanged with that of another user in the id parameter.
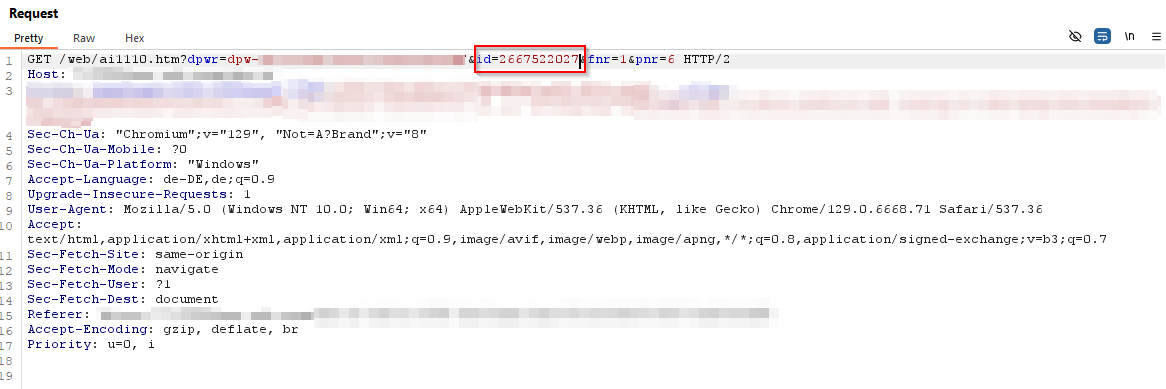
After this, only the manipulated request needs to be forwarded to the server and the rest of the workflow for creating the course needs to be carried out via the user interface.
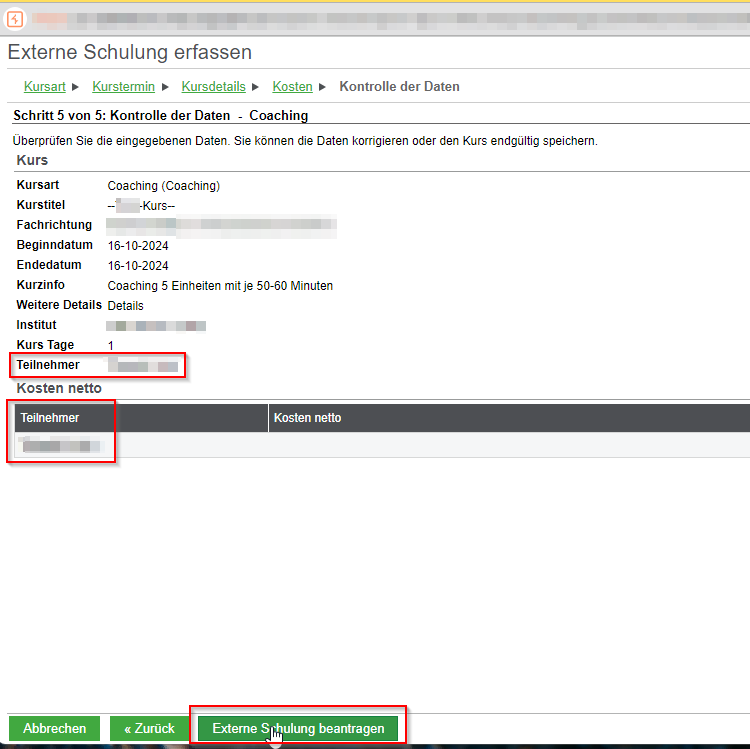
The following workflow step shows that the system has already successfully replaced the manipulated user ID with the foreign username.
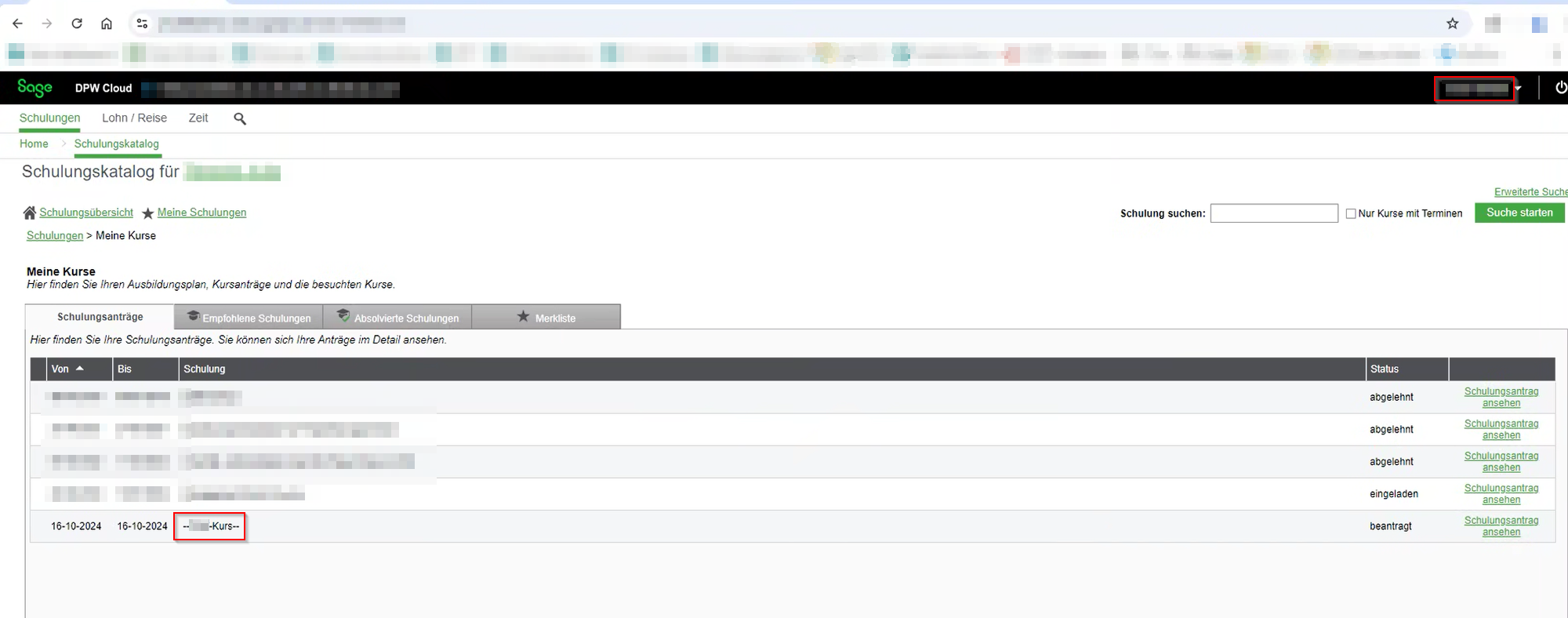
The course is then displayed to the external user in the personal overview.
Vendor contact timeline
| Date | Action |
|---|---|
| 2024-10-09 | Discovery of the vulnerability |
| 2024-10-24 | Initial contact to the vendor via info@sagedpw.at |
| 2024-10-31 | Second contact to the vendor via kundenservice@sagedpw.at due to no response |
| 2024-10-31 | Response from vendor |
| 2024-10-31 | Sharing a report on the vulnerability and its impact with the vendor |
| 2024-12-03 | Vendor confirms the vulnerability |
| 2024-12-03 | Vendor informs that the vulnerability will be fixed with version 2024_12_001 |
| 2024-12-06 | Disclosure of the vulnerability to MITRE |
| 2025-02-07 | MITRE assigns CVE-2024-56883 |
| 2025-02-12 | Public disclosure of the vulnerability |