2 minutes
Stored Cross-Site Scripting in Sage DPW - CVE-2024-56882
Affected Product: Sage DPW
Affected Versions: < 2024_12_000
Fixed Version: 2024_12_000
CVE-Number: CVE-2024-56882
Severity: 7.6 (CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:U/C:H/I:H/A:L)
Discovered by Regina Kohl, BSc and Maximilian Zingerle, BSc
During a penetration test for a customer, the audit team discovered that Sage DPW is prone to multiple vulnerabilities, including a Stored Cross-Site Scripting (XSS) vulnerability. This vulnerability allows authenticated users with employee privileges to store and execute malicious JavaScript code that affects other users of the system, including those with manager roles.
Proof of Concept
The following code can be inserted with an employee user with the MA role and trigger a demo output which demonstrates the feasibility.
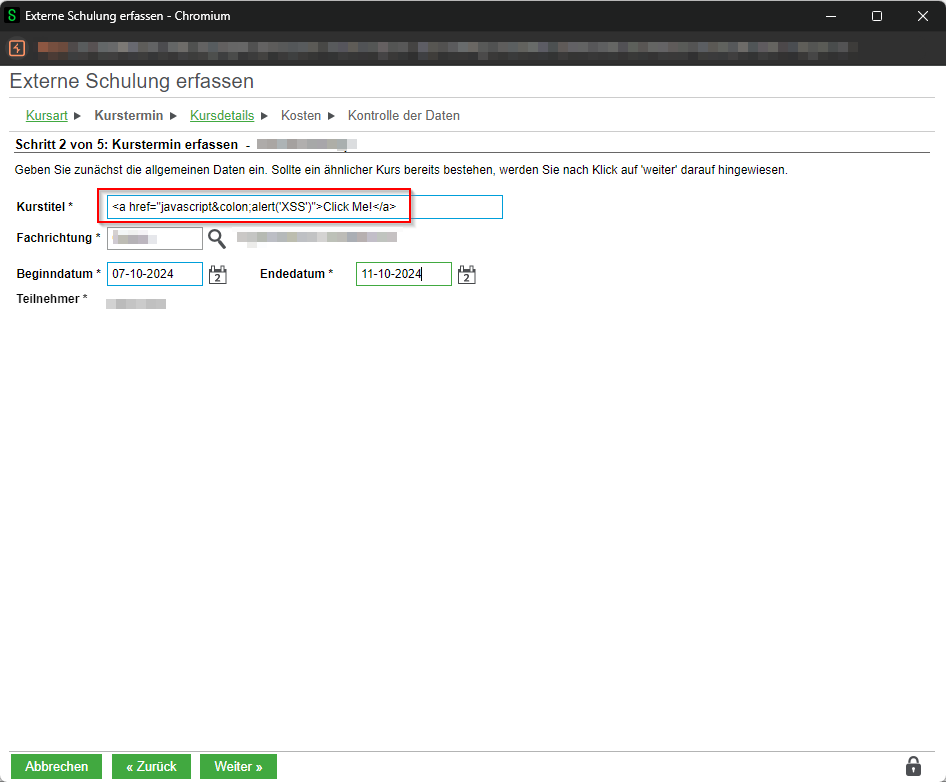
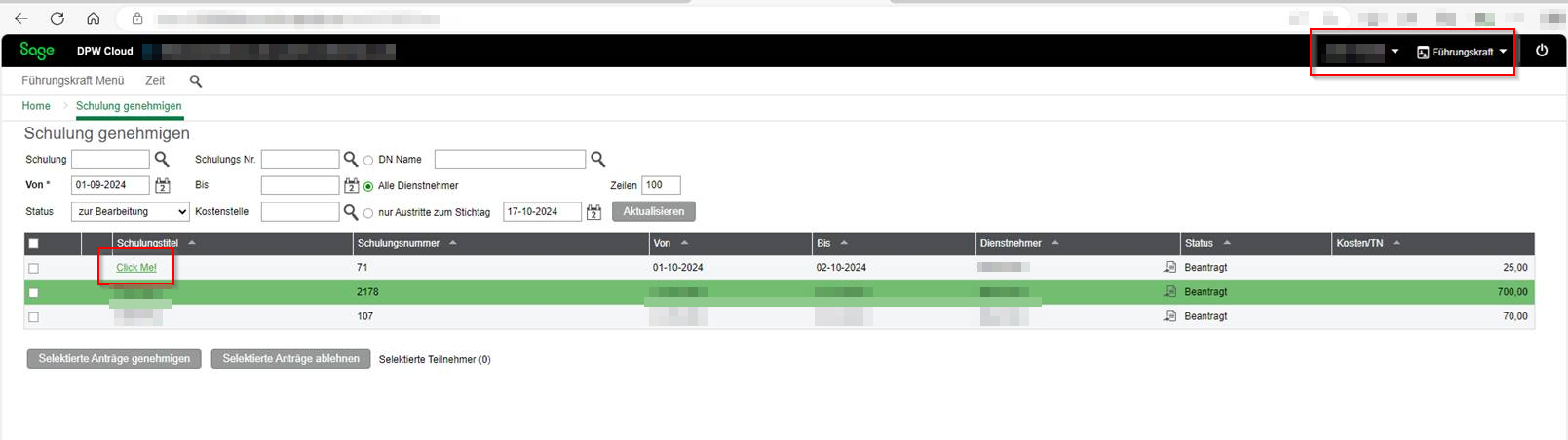
Kurstitel
External training courses can be created under Schulungen / Meine Schulungen / Externe Schulung. JavaScript code can be stored in the Kurstitel input field.
The following payload has been inserted for demonstration purposes:
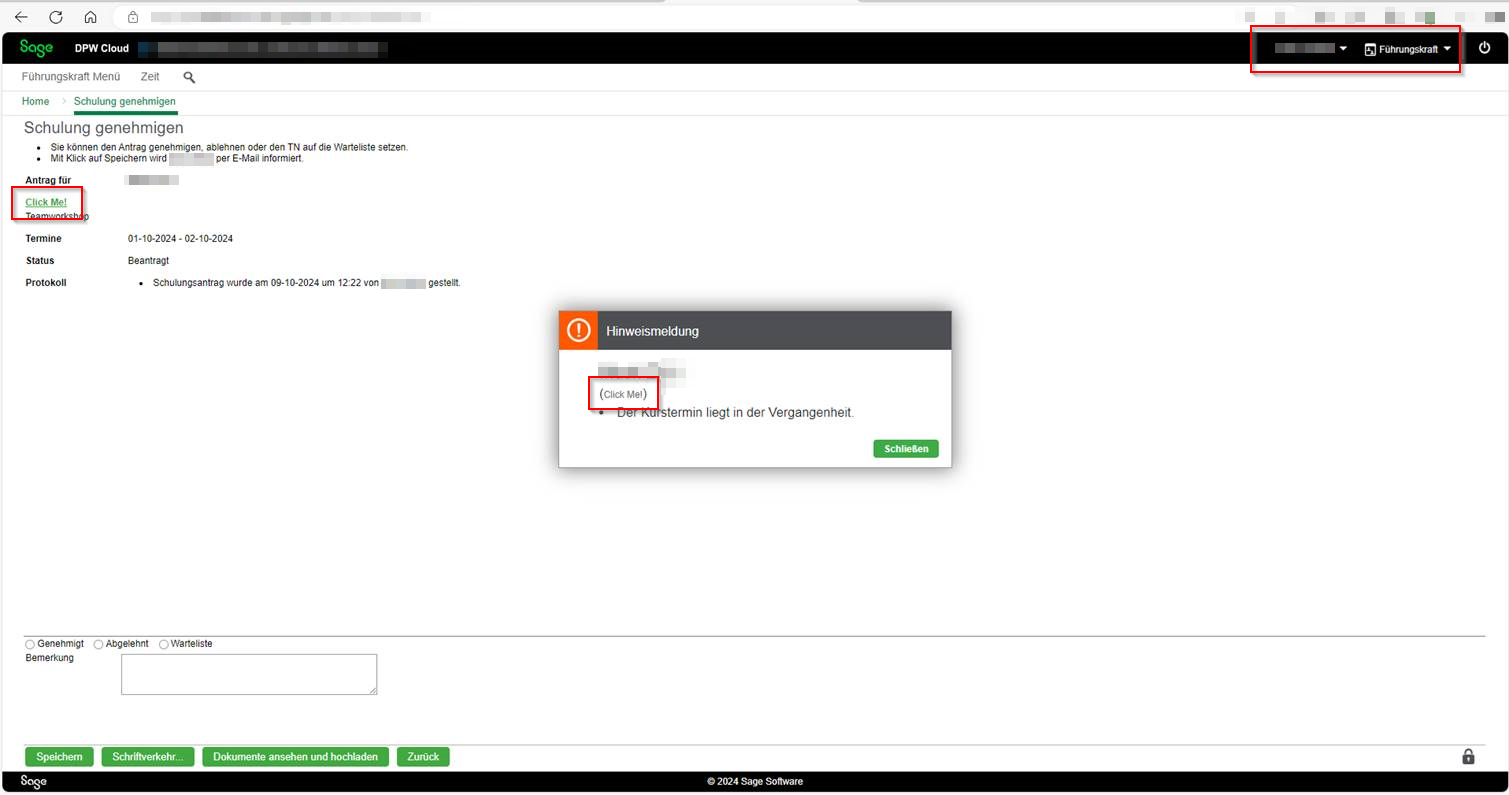
<a href="javascript:alert('XSS')">Click Me!</a>
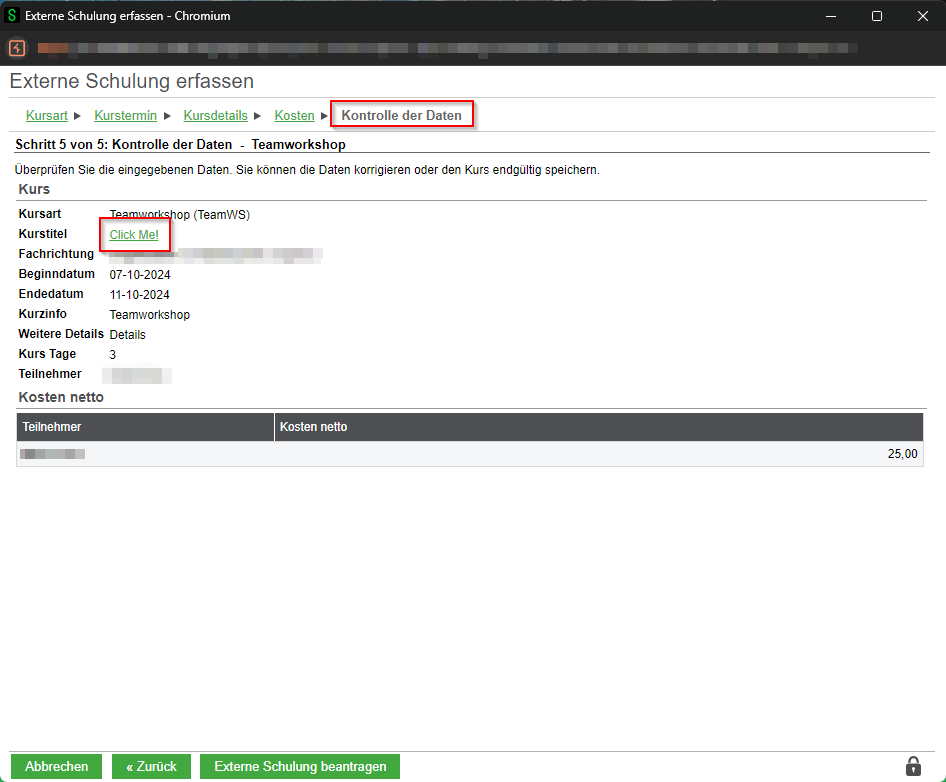
The JavaScript code is then interpreted in the last step of the creation process under “Kontrolle der Daten”, in the education overview, as well as in the overview “Meine Schulungen”. When a user clicks the injected link, the JavaScript code executes.
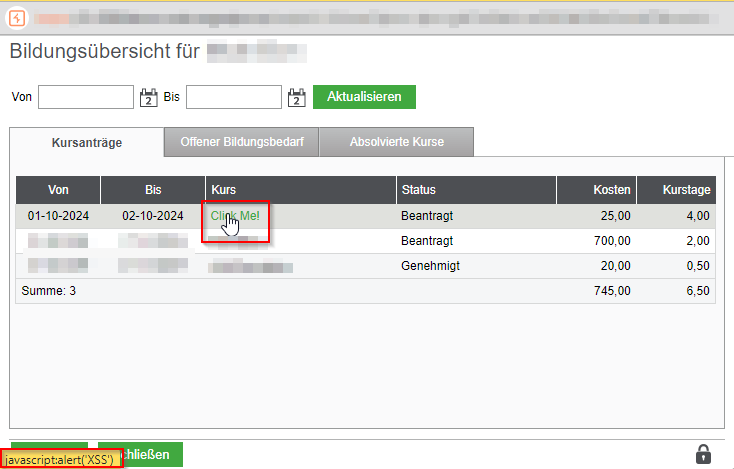
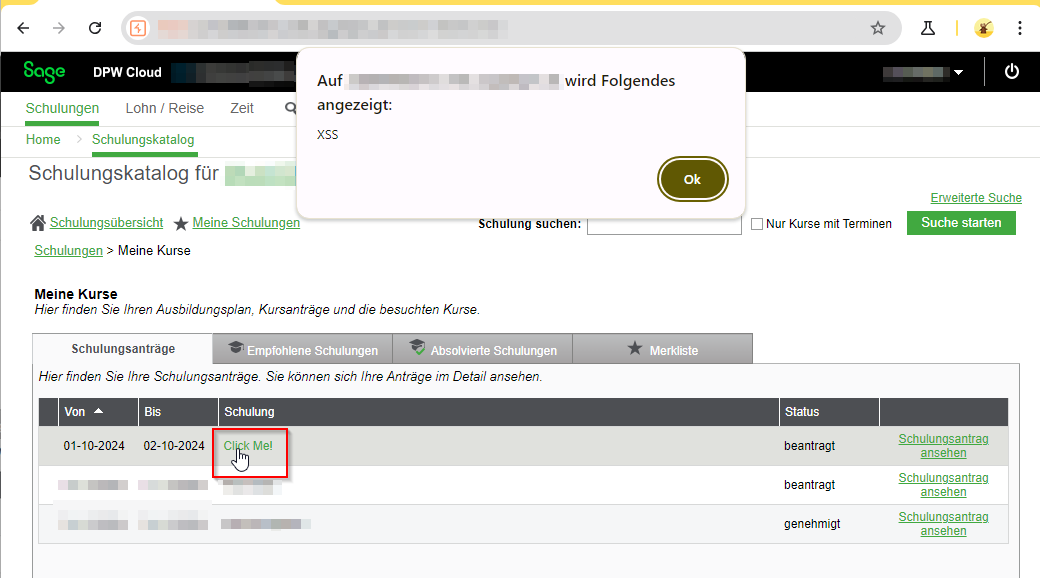
Furthermore, the payload is visible to users with the manager role, as shown below:
Kurzinfo
When creating external training courses, the above-mentioned payload can also be permanently stored in the Kurzinfo input field. However, the link inserted in “Kurzinfo” is not immediately visible in the overview, but appears when viewing the respective training request.
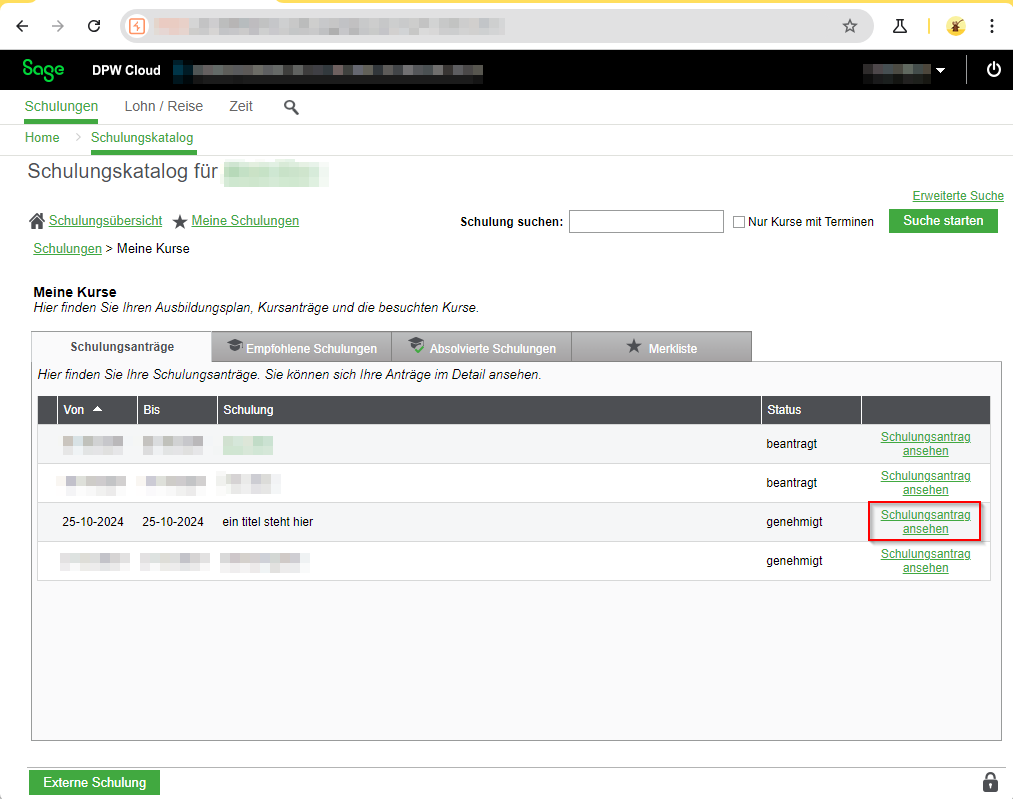
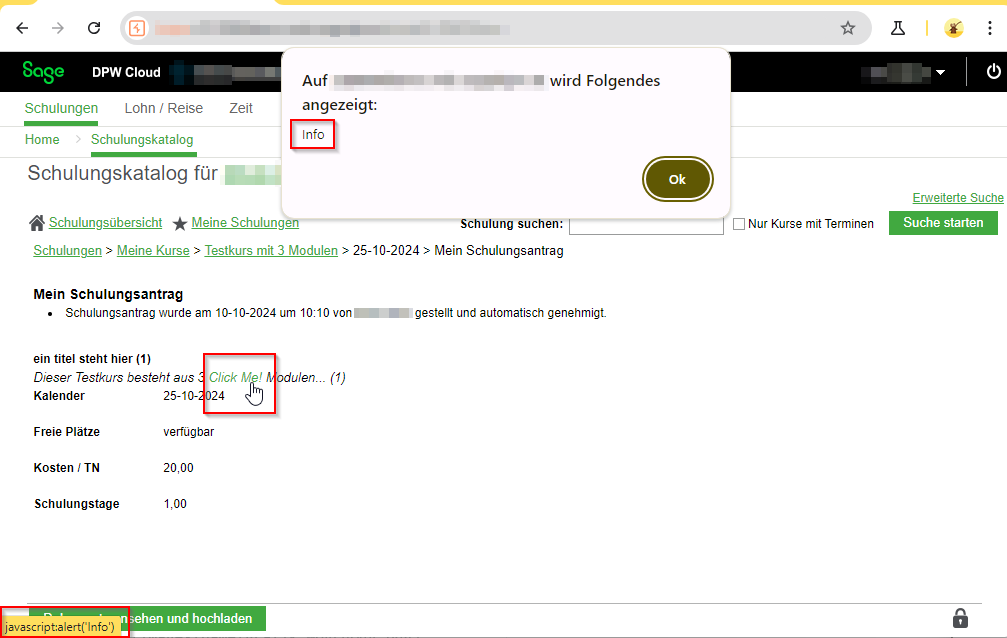
According to the vendor, the XSS payload is also executed for other users, including managers.
Vendor contact timeline
| Date | Action |
|---|---|
| 2024-10-09 | Discovery of the vulnerability |
| 2024-10-24 | Initial contact to the vendor via info@sagedpw.at |
| 2024-10-31 | Second contact to the vendor via kundenservice@sagedpw.at due to no response |
| 2024-10-31 | Response from vendor |
| 2024-10-31 | Sharing a report on the vulnerability and its impact with the vendor |
| 2024-11-06 | Vendor confirms the vulnerability |
| 2024-12-03 | Vendor informs that the vulnerability will be fixed with version 2024_12_000 |
| 2024-12-06 | Disclosure of the vulnerability to MITRE |
| 2025-02-07 | MITRE assigns CVE-2024-56882 |
| 2025-02-12 | Public disclosure of the vulnerability |