2 minutes
Stored and reflected XSS - CVE-2023-31434
Affected Product: Evasys
Affected Versions: evasys v8.2 Build 2275 - 2285 and evasys v9.0 Build 2400 (both according to vendor)
Fixed Version: v8.2 Build 2286 and v9.0 Build 2401
CVE-Number: CVE-2023-31434
Severity: 7,6 (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:H/A:L)
Discovered by Dipl-Ing. Mario Rubak, BSc MSc and Regina Kohl, BSc
The web application has numerous persistent and reflected XSS vulnerabilities that have been identified.
Proof of Concept
For example, in the user profile, JavaScript or HTML code can be injected into the GUI fields such as “Titel,” “Vorname,” and “Nachname,” which can be executed by the browser in various places within the web application.
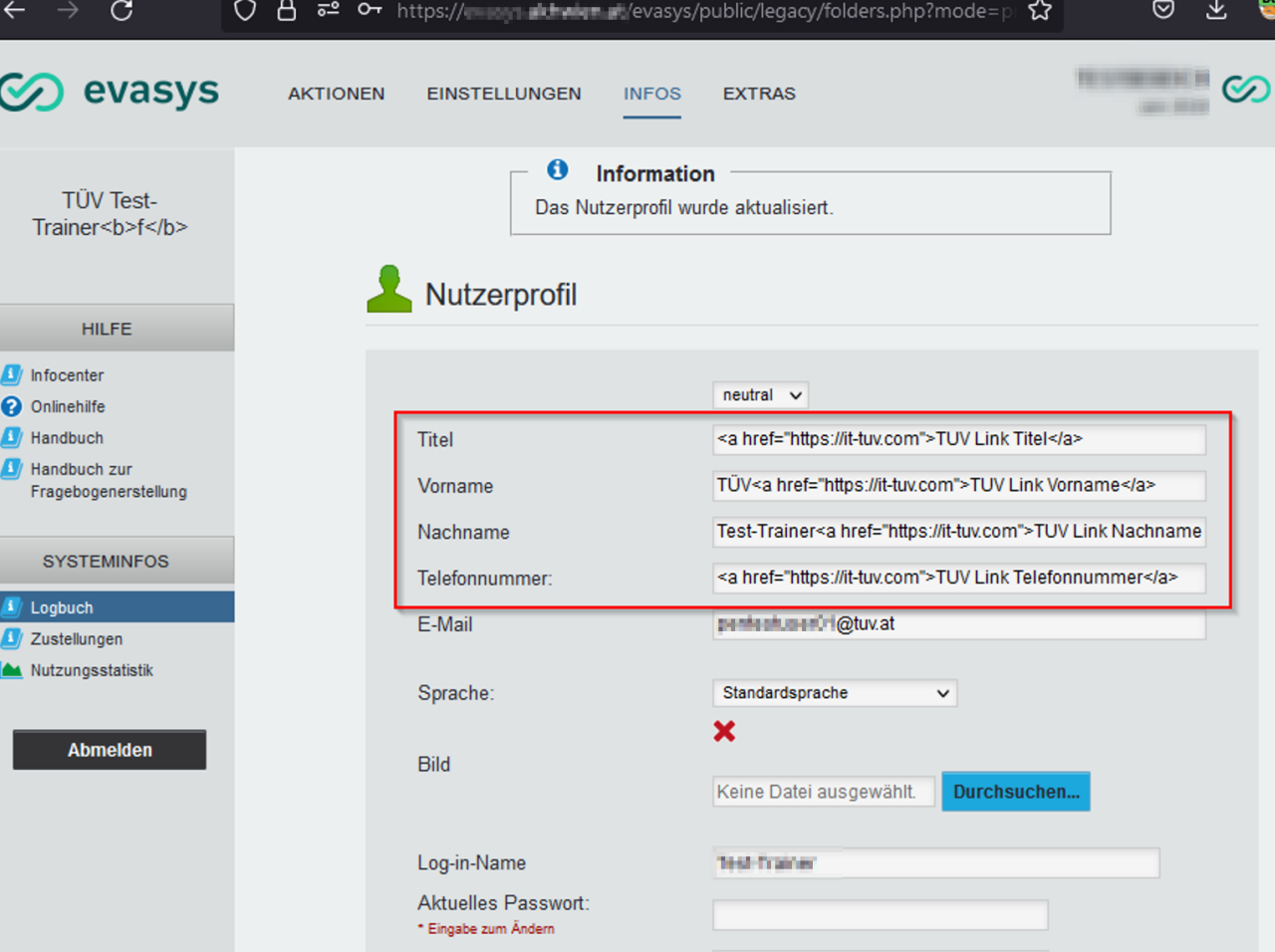
The HTML code is executed, but not the JavaScript code, in the following view:
Payload:
<a href=”https://it-tuv.com”>TUV Link</a>
Point of Execution:
https://example.com/evasys/public/online/index/preview?surveyid=1981652331&frmid=2142&nLangID=0&sLang=de_com&ONLINEID=
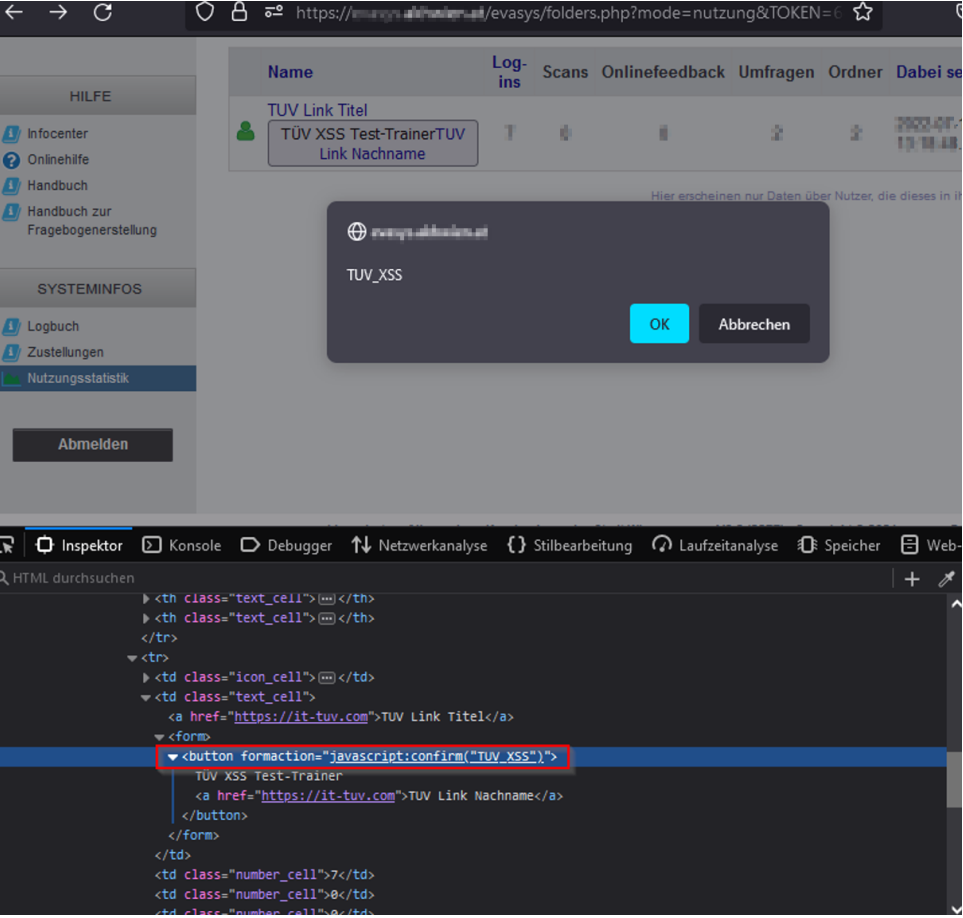
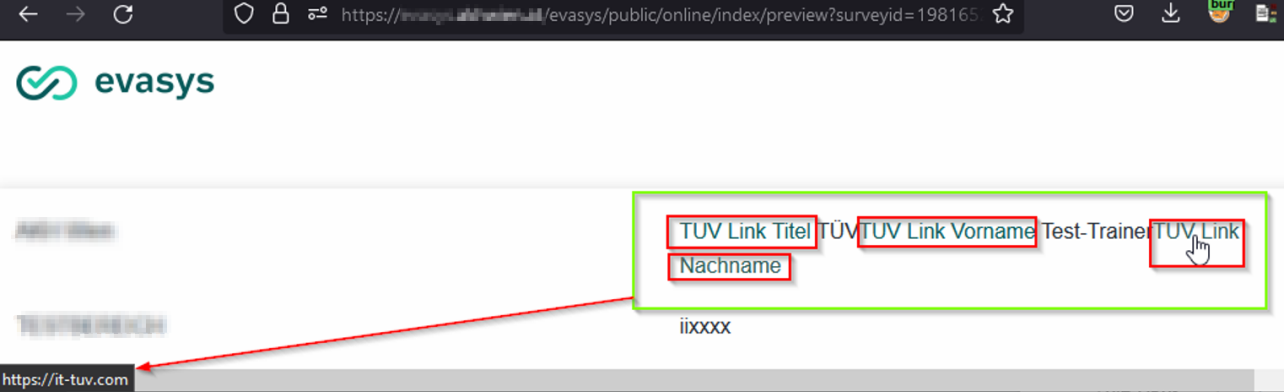 JavaScript code, on the other hand, is executed in at least two locations: the usage statistics page and the system status page. However, this is not an exhaustive list. The following example demonstrates the execution of JavaScript code on the usage statistics page.
JavaScript code, on the other hand, is executed in at least two locations: the usage statistics page and the system status page. However, this is not an exhaustive list. The following example demonstrates the execution of JavaScript code on the usage statistics page.
Payload:
<form><button formaction=javascript:confirm("TUV_XSS")>TÜV XSS
Point of Execution:
https://example.com/evasys/folders.php?mode=nutzung&TOKEN=<censored>&sNewMenuitemID=UsageStatistics
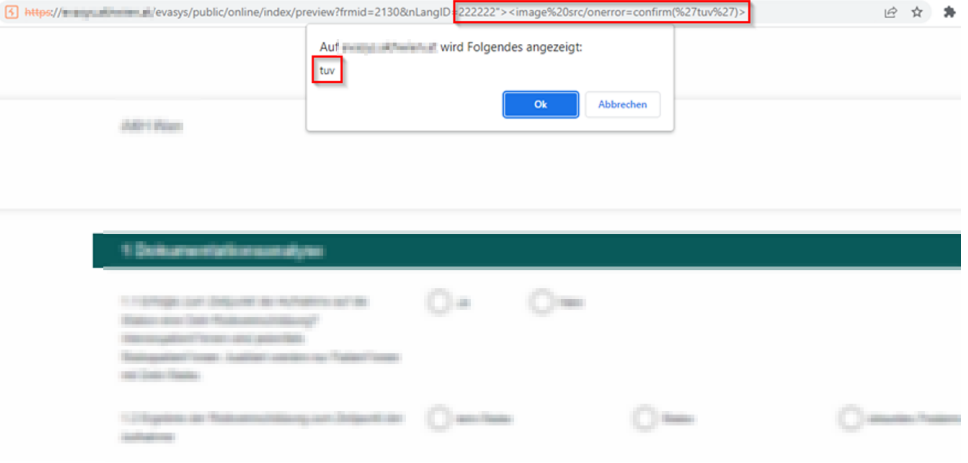
Additionally, a user with the role of “Trainer” can trigger a reflected XSS vulnerability by using the following link:
https://example.com/evasys/public/online/index/preview?frmid=2130&nLangID=222222%22%3E%3Cimage%20src/onerror=confirm('tuv')%3E
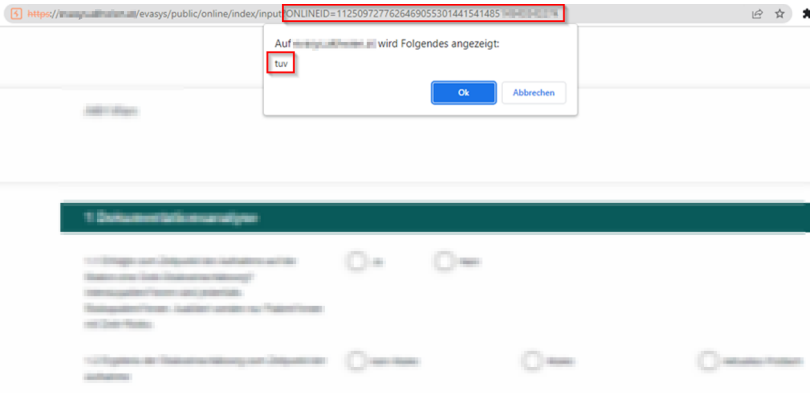
Afterwards, a link containing a server-generated online ID can be found in the server response.
https://example.com/evasys/public/online/index/input?ONLINEID=1125097277626469055301441541485<censored>
After generating the link with the online ID, a link without the payload can be found in the server response. This link can be sent to any unauthenticated person. When accessed, the survey will be displayed and the payload injected by the user with the Trainer role will be executed.
Vendor contact timeline
| Date | Action |
|---|---|
| 2022/07/26 | Discovery of the vulnerability |
| 2023/08/05 | Bulk disclosure of multiple vulnerabilities using the vendors support mail |
| 2023/08/08 | Vendors respond that they acknowledge the findings and start to work on a fix |
| 2023/08/10 | Evasys shares detailed plan for the fix with the researchers and asks for a few months of time before disclosing the vulnerability |
| 2023/08/23 | Vendor responds that the vulnerabilities will be fixed in version 8.2 and 9.0 in 2023/09/06 |
| 2023/01/02 | First attempt to request CVEs at MITRE |
| 2023/03/23 | Request was closed by MITRE without stating a reason |
| 2023/04/24 | Second attempt to request CVEs at MITRE |
| 2023/04/28 | MITRE assigns CVE-2023-31434 |
| 2023/05/02 | The Venord affirms that publication of the vulnerability is permissible |
| 2023/05/02 | CVE-2023-31434 has been published |