3 minutes
Usage of static secrets in Stimulsoft Designer - CVE-2023-25263
Affected Product: Stimulsoft Designer (Desktop), Stimulsoft Designer (Web)
Affected Versions: 2023.1.4 (confirmed), 2023.1.5 (confirmed), all prior versions (allegedly)
Fixed Version: Will not be fixed by the vendor
CVE-Number: CVE-2023-25263
Severity: 7.9 (CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:C/C:H/I:L/A:N)
Discovered by Ing. Simon Schönegger, BSc, MSc, Lejla Sarcevic, BSc, MSc, Dipl-Ing. Rainer Seyer, BSc
During a penetration test for a customer, the penetration testers identified that this customer was using Stimulsoft Reporting Designer (Web) 2023.1.3 as a tool to design and view specifically crafted reports for their customers. During this penetration test the researchers discovered that this version is prone to utilizes static secrets in order to encrypt the connection string in mrt files.
In order to exploit this vulnerability an attacker is only required to get hold of an mrt file which has an embedded SQL-Datasource. The knowledge of the secret can be obtained by decompiling the Stimulsoft application which does not use any obfuscation mechanism. It is notable that the secrets remained the same between different versions and installations. Therefore, the attacker only needs to know about the encryption key used in their installation and can decrypt connection strings of arbitrary reports with it. The secrets can be obtained by downloading the trial version of the product.
Proof of Concept
In order to prove this vulnerability, researchers created a sample report with a sample connection string to a
MS SQL Database embedded in it.
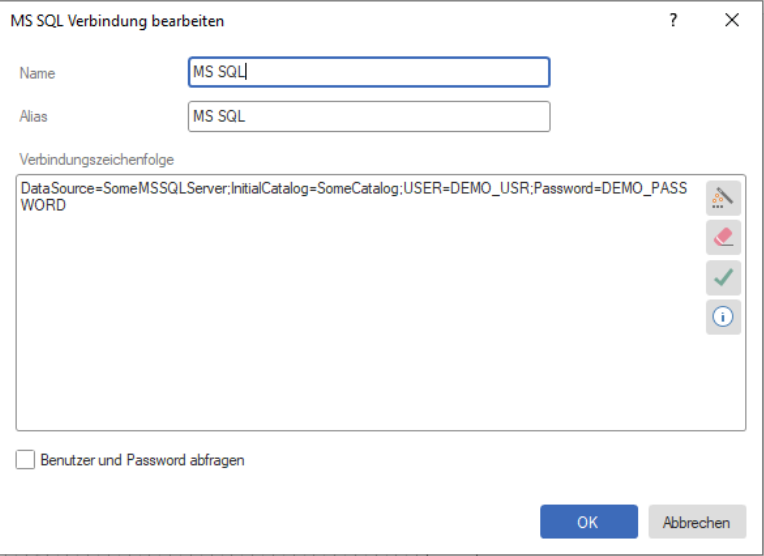 Connection strings are stored in the .mrt file. These connection strings are encrypted using a custom
function of Stimulsoft. The encrypted connection strings look like the following:
Connection strings are stored in the .mrt file. These connection strings are encrypted using a custom
function of Stimulsoft. The encrypted connection strings look like the following:
<Databases isList="true" count="1">
<MS_x0020_SQL Ref="2" type="Stimulsoft.Report.Dictionary.StiSqlDatabase" isKey="true">
<Alias>MS SQL</Alias>
<ConnectionStringEncrypted>
9BTRSM1MowV5FXnUekzhJ9F40etUa5KF4VrtfPpcLRf/bK3rV0+ykXJ4Zb
11hOPn3SyNaExUQvV5EyH4Yz3gf8Ram8JNe5O8a3vdpXr4brvlEtnLXW3S+Wxa
</ConnectionStringEncrypted>
<Name>MS SQL</Name>
</MS_x0020_SQL>
</Databases>
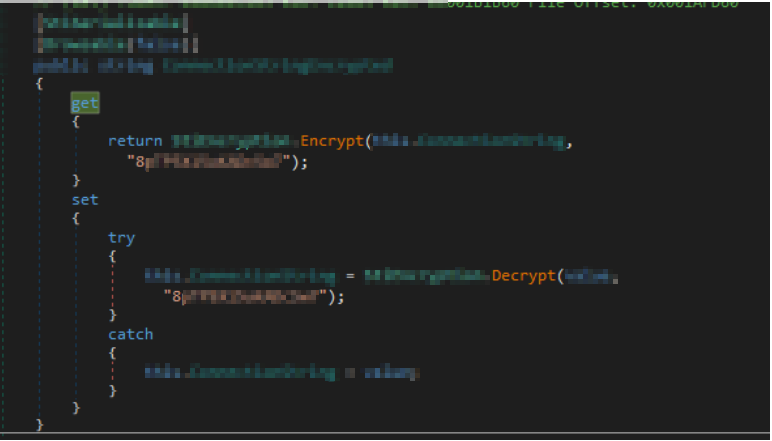
This connection string can not be decrypted using standard cryptographic methods without the knowledge of
the key. However, the researches decompiled the reporting designer and were able to get hold of the static
secret.
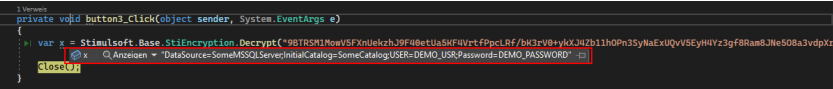
 Using this secret and example source code of Stimulsoft, which is available on Github, researchers were
able to quickly decrypt the connection string, since the example source code references all of the necessary
functions for decryption.
Using this secret and example source code of Stimulsoft, which is available on Github, researchers were
able to quickly decrypt the connection string, since the example source code references all of the necessary
functions for decryption.
Vendor contact timeline
| Date | Action |
|---|---|
| 2023/01/20 | Discovery of the vulnerability |
| 2023/01/20 | Bulk disclosure of multiple vulnerabilities using the vendors support mail |
| 2023/01/20 | Vendor responds that this encryption is only in place to obfuscate connection strings in HTTP requests and there is a possibility to add the connection string dynamically in the background code |
| 2023/01/21 | Researchers respond that connection strings should be treated as confidential and that it would be better to encrypt it by using user defined secrets, which should be entered when the report is opened in another instance |
| 2023/01/30 | Vendor responds that the do not see a way to change this behaviour. Therefore it will not be fixed. |
| 2023/01/30 | Disclosure of the vulnerability to MITRE |
| 2023/03/02 | MITRE assigns CVE-2023-25263 |
| 2023/03/02 | Researchers inform vendor about the CVE assignment |