2 minutes
SSRF in Stimulsoft Designer - CVE-2023-25262
Affected Product: Stimulsoft Designer (Web)
Affected Versions: 2023.1.3 (confirmed) 2023.1.4 (allegedly)
Fixed Version: Will not be fixed by the vendor
CVE-Number: CVE-2023-25262
Severity: 5.4 (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:C/C:L/I:L/A:N)
Discovered by Ing. Simon Schönegger, BSc, MSc, Lejla Sarcevic, BSc, MSc, Dipl-Ing. Rainer Seyer, BSc
During a penetration test for a customer, the penetration testers identified that this customer was using Stimulsoft Reporting Designer (Web) 2023.1.3 as a tool to design and view specifically crafted reports for their customers. During this penetration test the researchers discovered that this version is prone to server side request forgery.
The Reporting Designer (Web) offers the possibility to embed sources from external locations. If the user chooses an external location, the request to that resource is performed by the server rather than the client. Therefore, the server causes outbound traffic and potentially imports data. An attacker may also leverage this behaviour to exfiltrate data of machines on the internal network of the server hosting the Stimulsoft Reporting Designer (Web).
No privileges are required to execute this exploit if the reporting viewer or designer are embedded in a page which lacks authentication. Since the authentication and authorization are measurements that the person who embeds the viewer and designer must implement, the privileges that are required to exploit this vulnerability are referenced as “None”.
Proof of Concept
For this Proof of Concept, the web based Reporting Designer will try to import a CSV-File from a remote connection. (Note: This proof of concept is performed on the online trial of the Reporting Designer hosted on https://designer.stimulsoft.com/)
The payload for this Proof of Concept is https://<Collaborator>/evil.csv.
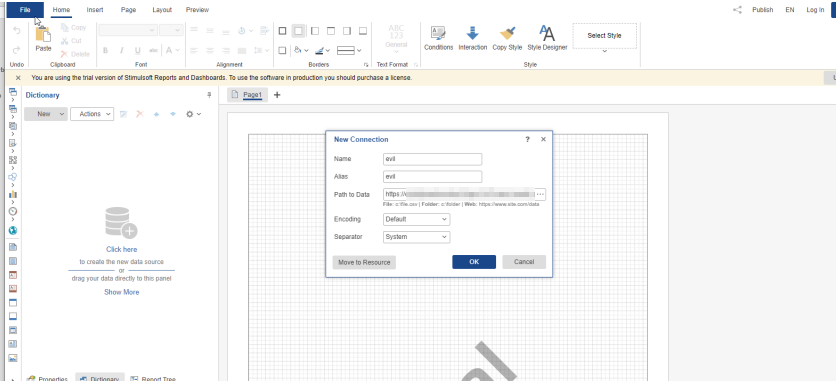
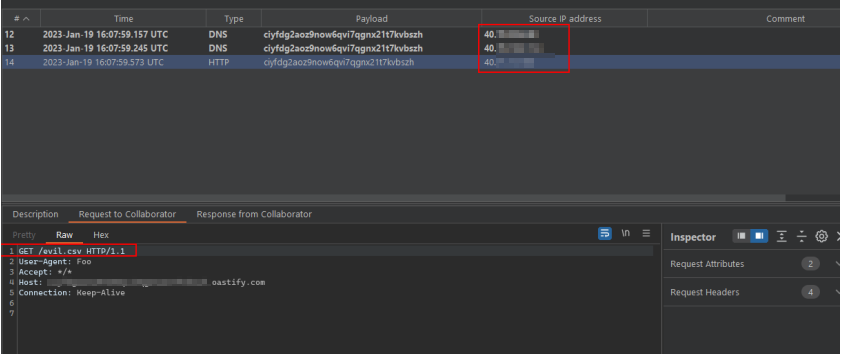 In this case, the reporting designer is hosted in Azure. This behaviour heavily depends on the clients
deployment, since this can very well be hosted on premise, which leads to an increased attack surface.
In this case, the reporting designer is hosted in Azure. This behaviour heavily depends on the clients
deployment, since this can very well be hosted on premise, which leads to an increased attack surface.
Vendor contact timeline
| Date | Action |
|---|---|
| 2023/01/16 | Discovery of the vulnerability |
| 2023/01/20 | Bulk disclosure of multiple vulnerabilities using the vendors support mail |
| 2023/01/20 | Vendor responds that this functionality was added by design |
| 2023/01/21 | Researchers provide advisory on how such vulnerability could be mitigated |
| 2023/01/30 | Vendor responds that “If you want to eliminate this vulnerability, you need to take care of it yourself” and that the proper use is the responsibility of the end developer. The vendor makes it clear that they will not fix this vulnerability |
| 2023/01/30 | Disclosure of the vulnerability to MITRE |
| 2023/03/02 | MITRE assigns CVE-2023-25262 |
| 2023/03/02 | Researchers inform vendor about the CVE assignment |