3 minutes
LFI in Stimulsoft Designer - CVE-2023-25260
Affected Product: Stimulsoft Designer (Web)
Affected Versions: 2023.1.3 (confirmed) 2023.1.4 (allegedly)
Fixed Version: 2023.2.1
CVE-Number: CVE-2023-25260
Severity: 8.6 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:N/A:N)
Discovered by Ing. Simon Schönegger, BSc, MSc, Lejla Sarcevic, BSc, MSc, Dipl-Ing. Rainer Seyer, BSc
During a penetration test for a customer, the penetration testers identified that this customer was using Stimulsoft Reporting Designer (Web) 2023.1.3 as a tool to design and view specifically crafted reports for their customers. During this penetration test the researchers discovered that this version is prone to local file inclusion.
The web version of the Reporting Designer offers the possibility to use a wide variety of local files as
Datasource. When selecting a file, the Reporting Designer opens a file selection dialog. However, if the user
does not open this dialog and simply inputs a path like C:\windows\temp\localfile.json the software will read
this file from the filesystem of the server. Which files may be read depends on the privileges of the user
which is used for starting the webserver. If a client runs the webserver as a high privileged user almost all
files can be read. This vulnerability can be combined with remote code execution in order to present data
without rendering it in the report.
No privileges are required to execute this exploit if the reporting viewer or designer are embedded in a page which lacks authentication. Since the authentication and authorization are measurements that the person who embeds the viewer and designer must implement, the privileges that are required to exploit this vulnerability are referenced as “None”.
Proof of Concept
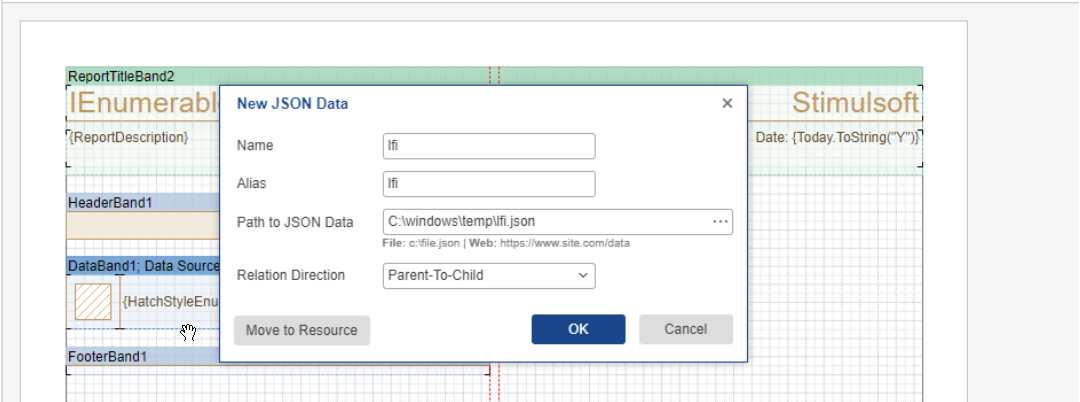
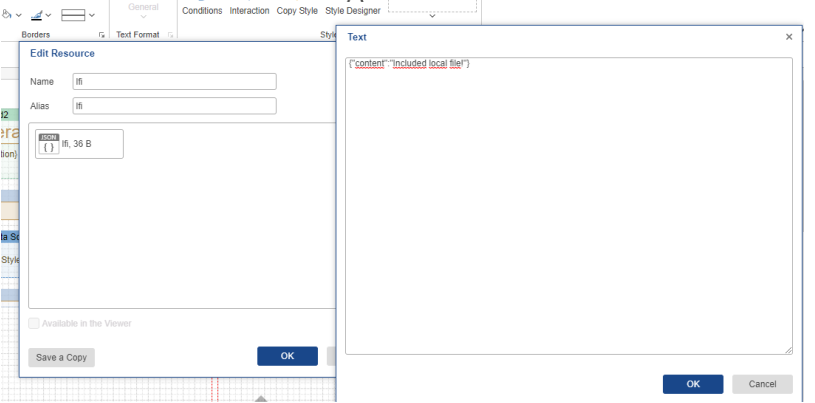
For this Proof of Concept, the file C:\windows\temp\lfi.json is placed on the server. This file is included in a
JSON datasource. When the included file is moved to a resource, the designer is able to see the content of
the file
Vendor contact timeline
| Date | Action |
|---|---|
| 2023/01/16 | Discovery of the vulnerability |
| 2023/01/20 | Bulk disclosure of multiple vulnerabilities using the vendors support mail |
| 2023/01/20 | Vendor responds that this functionality was added by design |
| 2023/01/21 | Researchers respond that this vulnerability can read all XML and JSON like files including web.config and appsettings.json and advises to fix this vulnerability |
| 2023/01/30 | Vendor responds that they have added an additional configuration option to avoid loading local files which will be added in the march release |
| 2023/01/30 | Disclosure of the vulnerability to MITRE |
| 2023/03/02 | MITRE assigns CVE-2023-25260 |
| 2023/03/02 | Researchers inform vendor about the CVE assignment and ask when the march version will be released |
| 2023/03/02 | Vendor responds that the version to fix this vulnerability will be released in the second part of march |
| 2023/03/02 | Agreement to publish the vulnerability as soon as the fix is released |